Posts tagged ‘April Fools Day’
Broad New Hacking Attack Detected
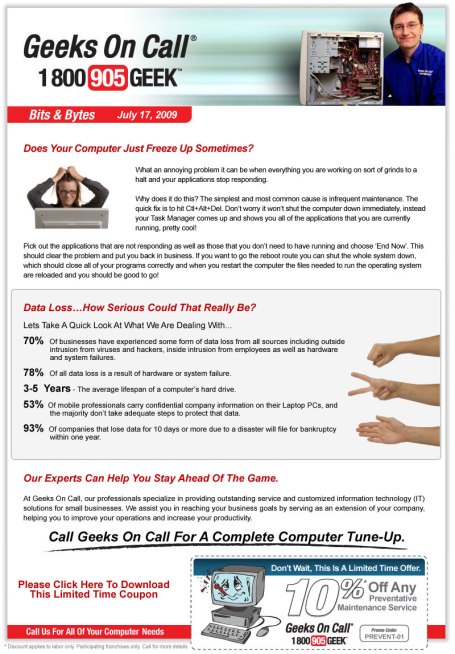
Global Offensive Snagged Corporate, Personal Data at nearly 2,500 Companies; Operation Is Still Running
Hackers in Europe and China successfully broke into computers at nearly 2,500 companies and government agencies over the last 18 months in a coordinated global attack that exposed vast amounts of personal and corporate secrets to theft, according to a computer-security company that discovered the breach.
The damage from the latest cyberattack is still being assessed, and affected companies are still being notified. But data compiled by NetWitness, the closely held firm that discovered the breaches, showed that hackers gained access to a wide array of data at 2,411 companies, from credit-card transactions to intellectual property.
The hacking operation, the latest of several major hacks that have raised alarms for companies and government officials, is still running and it isn’t clear to what extent it has been contained, NetWitness said. Also unclear is the full amount of data stolen and how it was used. Two companies that were infiltrated, pharmaceutical giant Merck & Co. and Cardinal Health Inc., said they had isolated and contained the problem.
Starting in late 2008, hackers operating a command center in Germany got into corporate networks by enticing employees to click on contaminated Web sites, email attachments or ads purporting to clean up viruses, NetWitness found.
In more than 100 cases, the hackers gained access to corporate servers that store large quantities of business data, such as company files, databases and email.
They also broke into computers at 10 U.S. government agencies. In one case, they obtained the user name and password of a soldier’s military email account, NetWitness found. A Pentagon spokesman said the military didn’t comment on specific threats or intrusions.
At one company, the hackers gained access to a corporate server used for processing online credit-card payments. At others, stolen passwords provided access to computers used to store and swap proprietary corporate documents, presentations, contracts and even upcoming versions of software products, NetWitness said.
Data stolen from another U.S. company pointed to an employee’s apparent involvement in criminal activities; authorities have been called in to investigate, NetWitness said. Criminal groups have used such information to extort sensitive information from employees in the past.
The spyware used in this attack allows hackers to control computers remotely, said Amit Yoran, chief executive of NetWitness. NetWitness engineer Alex Cox said he uncovered the scheme Jan. 26 while installing technology for a large corporation to hunt for cyberattacks.
That discovery points to the growing number of attacks in recent years that have drafted computers into cyber armies known as botnets—intrusions not blocked by standard antivirus software. Researchers estimate millions of computers are conscripted into these armies.
“It highlights the weaknesses in cyber security right now,” said Adam Meyers, a senior engineer at government contractor SRA International Inc. who reviewed the NetWitness data. “If you’re a Fortune 500 company or a government agency or a home DSL user, you could be successfully victimized.”
Disclosure of the attack comes on the heels of Google Inc.’s allegation that it and more than 20 other companies were breached by Chinese hackers. This operation appears to be more far-reaching, infiltrating some 75,000 computers and touching 196 countries. The highest concentrations of infected computers are in Egypt, Mexico, Saudi Arabia, Turkey and the U.S.
NetWitness, based in Herndon, Va., said it was sharing information with the companies infected. Mr. Yoran declined to name them. The company provides computer security for U.S. government agencies and companies. Mr. Yoran is a former Air Force officer who also served as cyber security chief at the Department of Homeland Security.
Besides Merck and Cardinal Health, people familiar with the attack named several other companies infiltrated, including Paramount Pictures and software company Juniper Networks Inc.
Merck said in a statement that one computer had been infected. It said it had isolated the attack and that “no sensitive information was compromised.”
Cardinal said it removed the infected computer from its network. Paramount declined to comment. Juniper’s security chief, Barry Greene, wouldn’t speak about any specific incidents but said the company worked aggressively to counter infections.
Journal CommunityDISCUSS
“The key is not to pour money into protecting information, but to develop a global approach to neutralizing its value. By creating secrets, we have created value, which is pursued by opportunists. ”
—John M. Brock
NetWitness, which does extensive work for the U.S. government and private-sector clients, said it was sharing its information with the Federal Bureau of Investigation. The FBI said it received numerous allegations about potential compromises of network systems and responded promptly, in coordination with law-enforcement partners.
The computers were infected with spyware called ZeuS, which is available free on the Internet in its basic form. It works with the FireFox browser, according to computer-security firm SecureWorks. This version included a $2,000 feature that works with FireFox, according to SecureWorks.
Evidence suggests an Eastern European criminal group is behind the operation, likely using some computers in China because it’s easier to operate there without being caught, said NetWitness’s Mr. Yoran.
There are some electronic fingerprints suggesting the same group was behind a recent effort to dupe government officials and others into downloading spyware via emails purporting to be from the National Security Agency and the U.S. military, NetWitness’s Mr. Yoran said.
That attack was described in a Feb. 5 report from the Department of Homeland Security, which said it was issuing an alert to the government and other organizations to “prevent further compromises.”
A DHS official said that ZeuS was among the top five reported tools for malware infections.
Click Here To Chat With A Representative Now
Call us today 1-800-905-GEEK (4335) or visit us online www.geeksoncall.com
By SIOBHAN GORMAN
U.S. Government Computers Targeted In Massive Cyber Attack
By LOLITA C. BALDOR, Associated Press Writer Lolita C. Baldor, Associated Press Writer
The powerful attack that overwhelmed computers at U.S. and South Korean government agencies for days was even broader than initially realized, also targeting the White House, the Pentagon and the New York Stock Exchange.
Other targets of the attack included the National Security Agency, Homeland Security Department, State Department, the Nasdaq stock market and The Washington Post, according to an early analysis of the malicious software used in the attacks. Many of the organizations appeared to successfully blunt the sustained computer assaults.
The Associated Press obtained the target list from security experts analyzing the attacks. It was not immediately clear who might be responsible or what their motives were. South Korean intelligence officials believe the attacks were carried out by North Korea or pro-Pyongyang forces.
The attack was remarkably successful in limiting public access to victim Web sites, but internal e-mail systems are typically unaffected in such attacks. Some government Web sites — such as the Treasury Department, Federal Trade Commission and Secret Service — were still reporting problems days after the attack started during the July 4 holiday. South Korean Internet sites began experiencing problems Tuesday.
South Korea’s National Intelligence Service, the nation’s principal spy agency, told a group of South Korean lawmakers Wednesday it believes that North Korea or North Korean sympathizers in the South were behind the attacks, according to an aide to one of the lawmakers briefed on the information.
The aide spoke on condition of anonymity, citing the sensitivity of the information. The National Intelligence Service — South Korea’s main spy agency — said it couldn’t immediately confirm the report, but it said it was cooperating with American authorities.
The attacks will be difficult to trace, said Professor Peter Sommer, an expert on cyberterrorism at the London School of Economics. “Even if you are right about the fact of being attacked, initial diagnoses are often wrong,” he said Wednesday.
Amy Kudwa, spokeswoman for the Homeland Security Department, said the agency’s U.S. Computer Emergency Readiness Team issued a notice to federal departments and other partner organizations about the problems and “advised them of steps to take to help mitigate against such attacks.”
New York Stock Exchange spokesman Ray Pellecchia could not confirm the attack, saying the company does not comment on security issues.
Attacks on federal computer networks are common, ranging from nuisance hacking to more serious assaults, sometimes blamed on China. U.S. security officials also worry about cyber attacks from al-Qaida or other terrorists.
This time, two government officials acknowledged that the Treasury and Secret Service sites were brought down, and said the agencies were working with their Internet service provider to resolve the problem. The officials spoke on condition of anonymity because they were not authorized to speak on the matter.
Ben Rushlo, director of Internet technologies at Keynote Systems, said problems with the Transportation Department site began Saturday and continued until Monday, while the FTC site was down Sunday and Monday.
Keynote Systems is a mobile and Web site monitoring company based in San Mateo, Calif. The company publishes data detailing outages on Web sites, including 40 government sites it watches.
According to Rushlo, the Transportation Web site was “100 percent down” for two days, so that no Internet users could get through to it. The FTC site, meanwhile, started to come back online late Sunday, but even on Tuesday Internet users still were unable to get to the site 70 percent of the time.
Web sites of major South Korean government agencies, including the presidential Blue House and the Defense Ministry, and some banking sites were paralyzed Tuesday. An initial investigation found that many personal computers were infected with a virus ordering them to visit major official Web sites in South Korea and the U.S. at the same time, Korea Information Security Agency official Shin Hwa-su said.
Associated Press writers Hyung-Jin Kim in Seoul, South Korea; Andrew Vanacore in New York; and Pan Pylas in London contributed to this report.
Protect Windows from a Botched Software Installation
Before you install any new program, you should create a “restore point”. Doing so will enable you to undo any problems or damage caused by the software installation. Here’s how:
- Click the Start button in the lower-left corner of Windows
- Click All Programs
- Select Accessories
- Select System Tools
- Click System Restore
- The System Restore window will open. Click the Create a Restore Point button
- Click Next
- Under the Restore Point Description heading, type some words or sentences that will help you to remember why you are creating this restore point. For example, if you just bought a new antivirus program, you could label this restore point “Before Installation of New Antivirus Software.” Of course if you are not a do it yourselfer or you take a shot at it and still have problems you can always call 1-800-905-GEEK to have a certified IT professional from Geeks On Call fix it right.
Conficker-C Worm Solution
Conficker-C Worm Solution / Solution / Instructions, support and more information on how to manually remove a Conficker/Downadup infection from a system have been published by major security vendors. Please see below for a few of those sites. Each of these vendors offers free tools that can verify the presence of a Conficker/Downadup infection and remove the worm:
Continue Reading April 1, 2009 at 5:43 pm geeksoncall 1 comment
Last-minute Conficker survival guide
Tomorrow — April 1 — is D-Day for Conficker, as whatever nasty payload it’s packing is currently set to activate. What happens come midnight is a mystery: Will it turn the millions of infected computers into spam-sending zombie robots? Or will it start capturing everything you type — passwords, credit card numbers, etc. — and send that information back to its masters?
No one knows, but we’ll probably find out soon.
Or not. As Slate notes, Conficker is scheduled to go “live” on April 1, but whoever’s controlling it could choose not to wreak havoc but instead do absolutely nothing, waiting for a time when there’s less heat. They can do this because the way Conficker is designed is extremely clever: Rather than containing a list of specific, static instructions, Conficker reaches out to the web to receive updated marching orders via a huge list of websites it creates. Conficker.C — the latest bad boy — will start checking 50,000 different semi-randomly-generated sites a day looking for instructions, so there’s no way to shut down all of them. If just one of those sites goes live with legitimate instructions, Conficker keeps on trucking.
Conficker’s a nasty little worm that takes serious efforts to bypass your security defenses, but you aren’t without some tools in your arsenal to protect yourself.
Your first step should be the tools you already have: Windows Update, to make sure your computer is fully patched, and your current antivirus software, to make sure anything that slips through the cracks is caught.
But if Conficker’s already on your machine, it may bypass certain subsystems and updating Windows and your antivirus at this point may not work. If you are worried about anything being amiss — try booting into Safe Mode, which Conficker prevents, to check — you should run a specialized tool to get rid of Conficker.
Microsoft offers a web-based scanner (note that some users have reported it crashed their machines; I had no trouble with it), so you might try one of these downloadable options instead: Symantec’s Conficker (aka Downadup) tool, Trend Micro’s Cleanup Engine, or Malwarebytes. Conficker may prevent your machine from accessing any of these websites, so you may have to download these tools from a known non-infected computer if you need them. Follow the instructions given on each site to run them successfully. (Also note: None of these tools should harm your computer if you don’t have Conficker.)
As a final safety note, all users — whether they’re worried about an infection or know for sure they’re clean — are also wise to make a full data backup today.
What won’t work? Turning your PC off tonight and back on on April 2 will not protect you from the worm (sorry to the dozens of people who wrote me asking if this would do the trick). Changing the date on your PC will likely have no helpful effect, either. And yes, Macs are immune this time out.
Yahoo Tech News – Tue Mar 31, 2009
Need More Assistance?
Call 1-800-905-GEEK (4335) Today
Mention Promo Code: APRIL25
and Receive $25.00 Off New Service
A new virus may be set to target computers on April Fool’s Day.
A new virus may be set to target computers on April Fool’s Day.
Continue Reading March 26, 2009 at 7:58 pm geeksoncall Leave a comment



Geeks On Call Celebrates Women’s Equality Day
If you have trouble reading this post simply click the link below to be taken to the Geeks On Call website view.
August 28, 2009 at 10:30 am geeksoncall Leave a comment